How to hunt for Malvertising ads on Android
This process was crafted after about 7 hours of trying different things in order to find malvertising ads. I was invited to a unique program and really wanted to find a valid submission because nobody had yet.
Setting up the testing environment
The testing environment had some requirements that were very unique. I couldn't use a proxy over wifi because the ads wouldn't pop-up otherwise only on the mobile network. I tried some local traffic capture apps and didn't have any luck with those either. Eventually I was successful with Android Dev-Tools with Chrome on desktop. Since I was on Android this turned out to be the best option.
Steps needed on Android cell phone
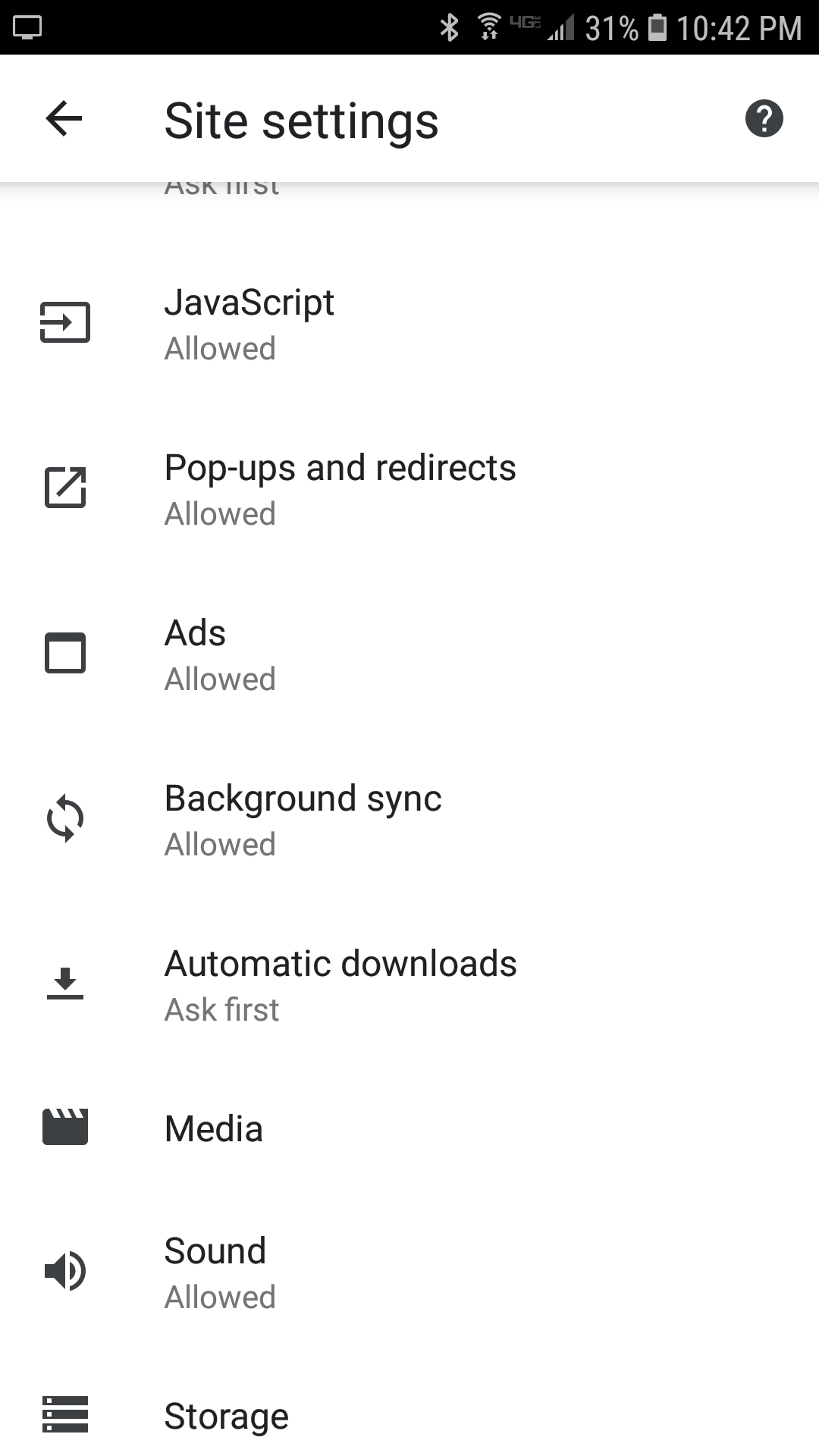
Steps needed on desktop with Chrome
Usually when installing Android Studio on desktop DevTools will also be installed. DevTools will detect your device when it is plugged into the computer via usb, accept the prompt on Android that looks like this screenshot.
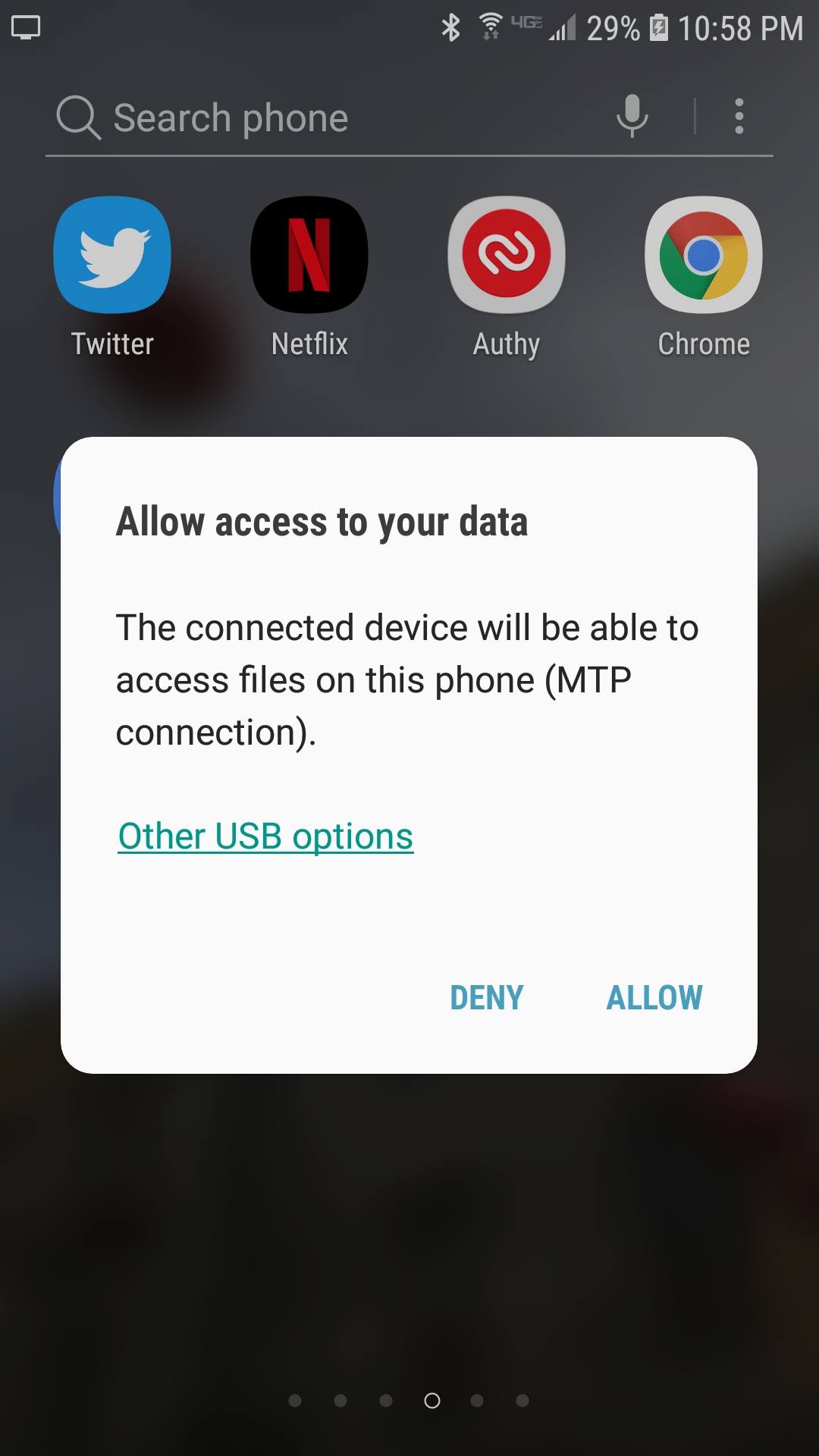
Now open Chrome and hold Ctrl+Shift+I to open DevTools and click Discover USB devices.
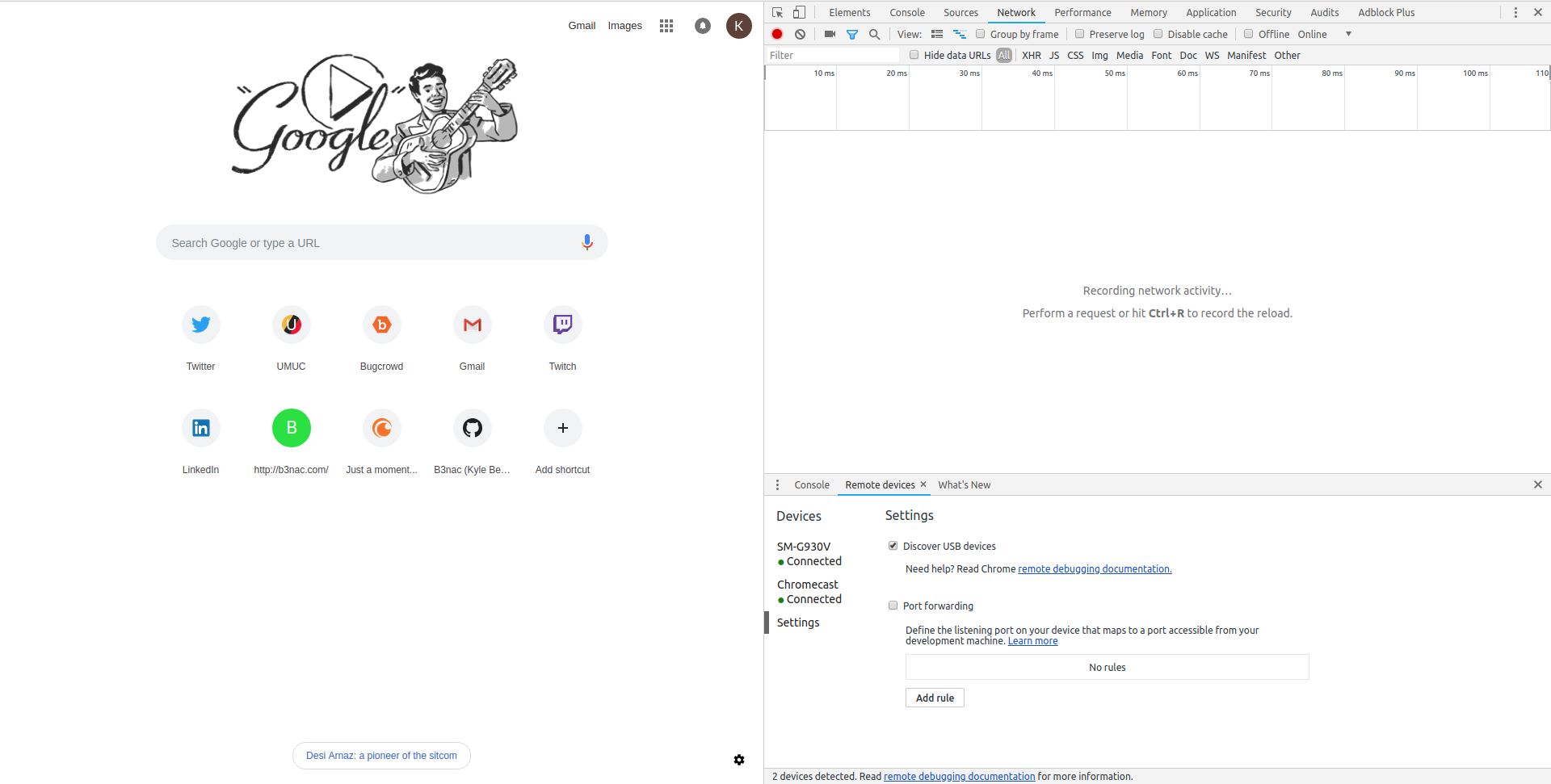
To find your device go to Network > Remote devices this is where you'll click on your phone in Chrome browser.
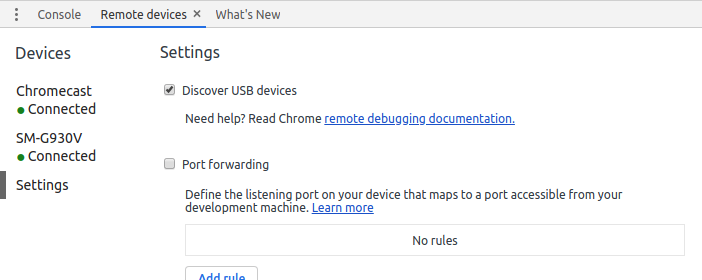
Next I will open Chrome on my Android device and the browser tab will be detected in the Remote Devices window.
Click inspect on the tab you want DevTools to monitor. A window will open showing your phone screen and all requests made while loading the tab. This is also a handy way to check if there are different requests on mobile compared to a desktop website. As an example I used my website.
Target websites
Because of the nondisclosure policy I can't say what websites I used this method on. The more ads that load through a bidding system the better. Attackers use this bidding system to sneak in their ads on websites. After you've found a website that loads a lot of ads you're in business.
How the malvertising payload fires
The malvertising ads work by winning a bid and using Polyglot images to hide malvertising attacks. The best way to try to intercept these Polyglot payloads is using DevTools and saving a log of requests. This way a HAR file can be saved and analyized after the payload fires.
The Method for Capturing the Redirect
The browsing needs to be as human as possible and not automated. This method worked for me every 5-8 minutes.
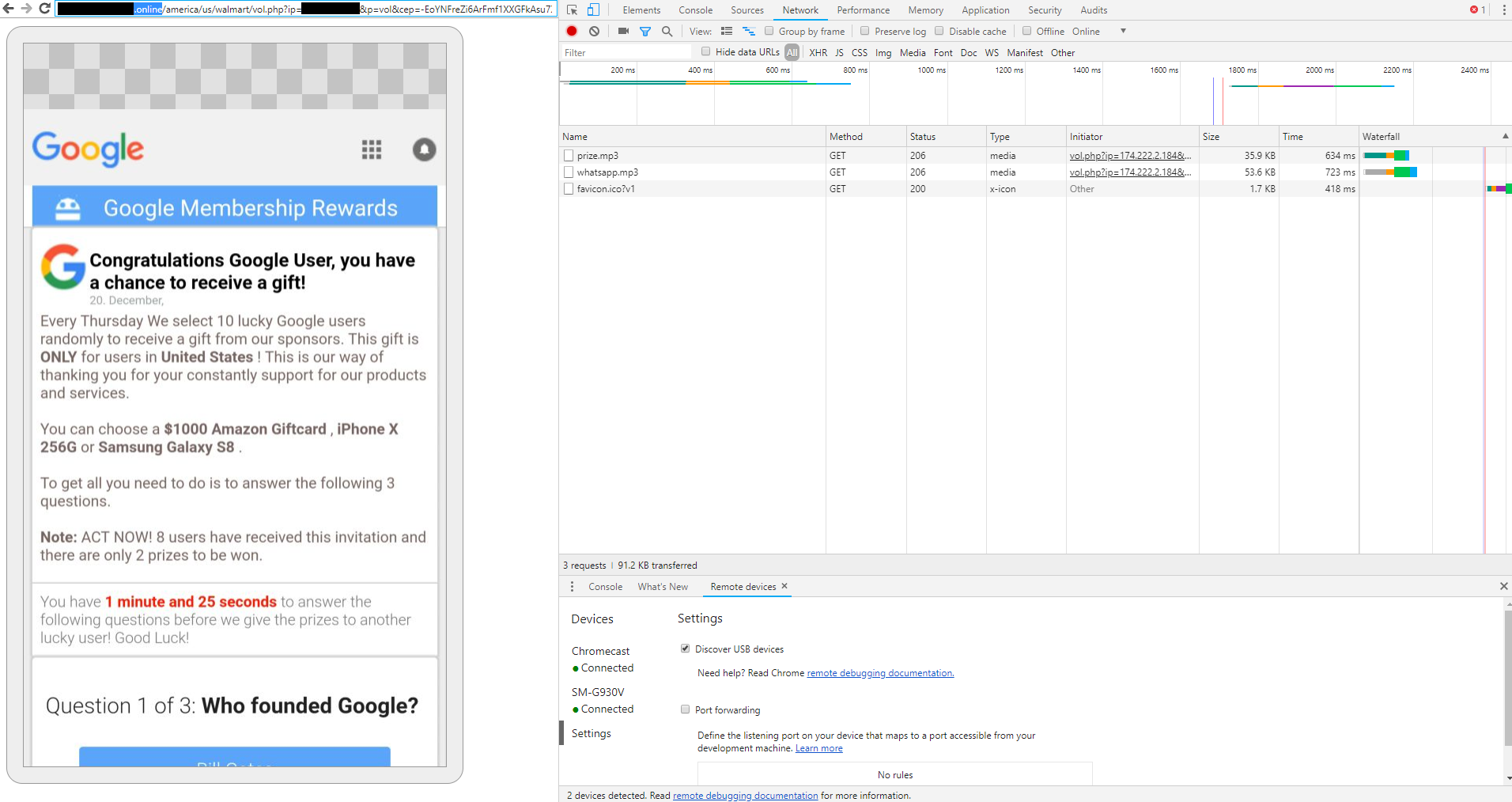
More examples of malvertising ads
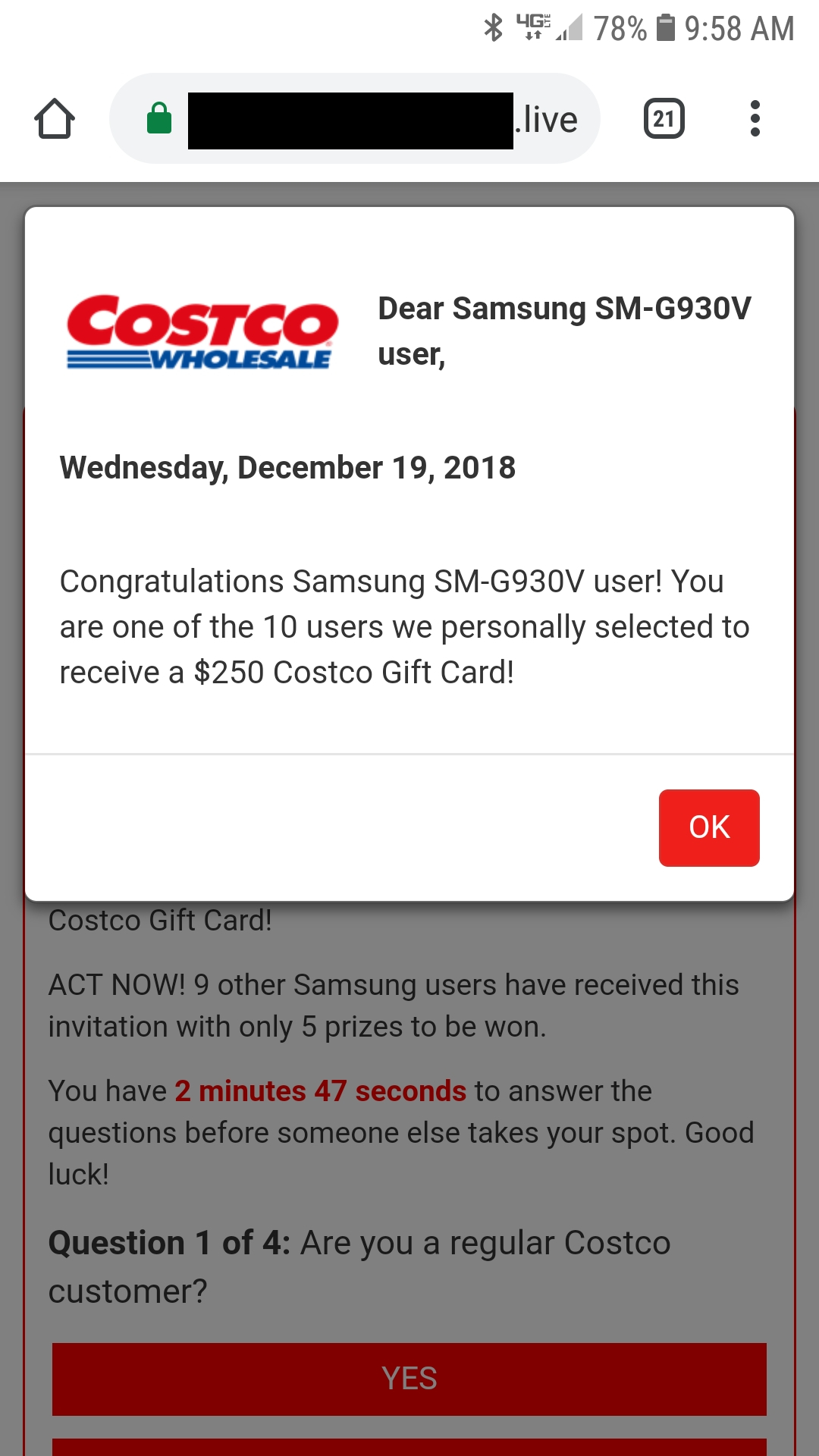
And another that targeted Google.
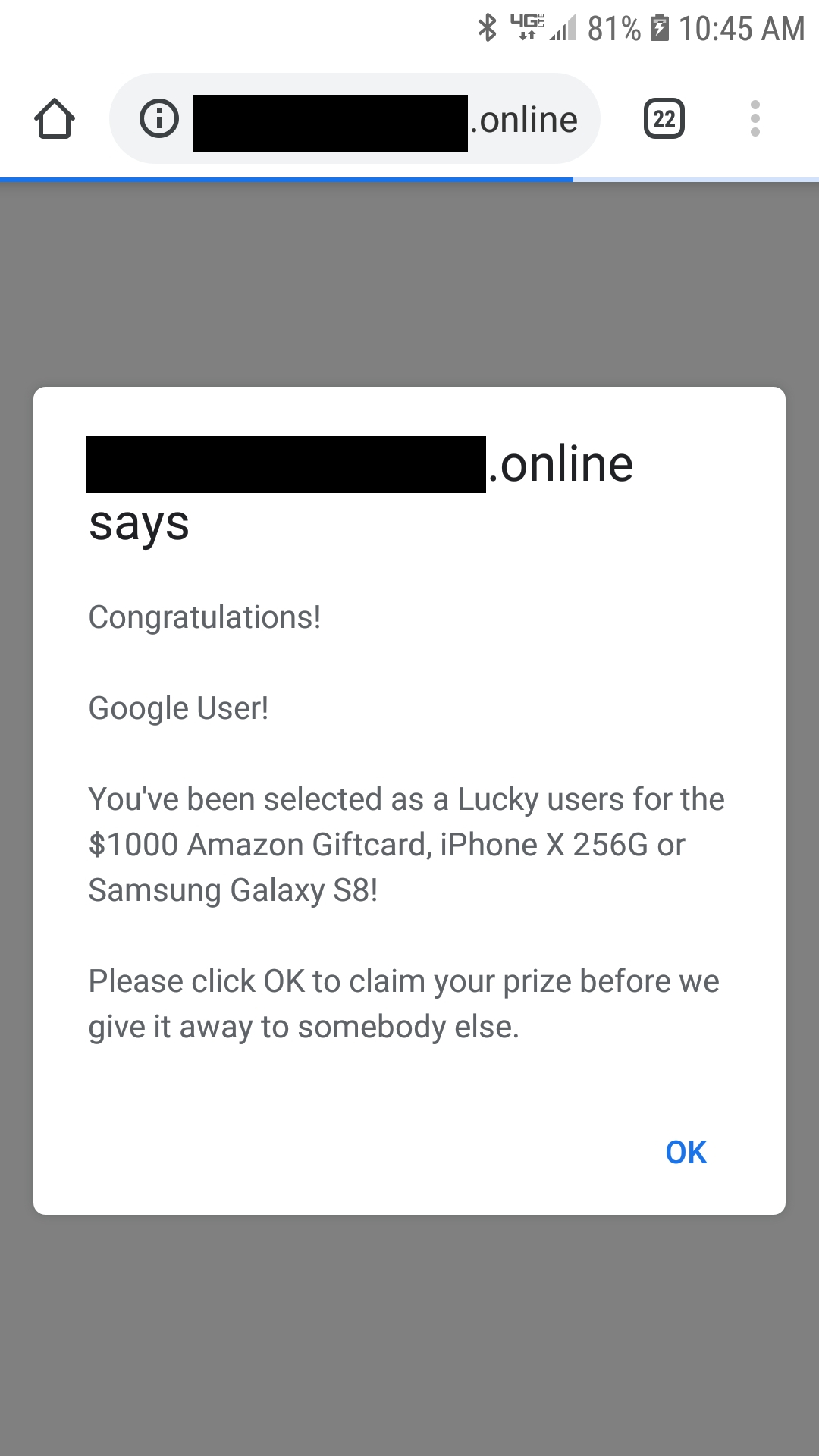
It's interesting that the urls have a one use token for the ad unless you had the initial redirect link. Also all domains were .live or .online. Another technique they used was a countdown timer to try to make it seem like the victim needed to make a selection within that time frame. Nothing happened after the timer hit 0. Thirdly increasing rewards with every redirect page eventually leading to a Costco copycat website.
Once an ad is triggered right click on any of the requests and select "Save all as HAR with content". This will save a HAR file as "website.har". A HAR file is a json formatted file of all requests made in the browsing session.
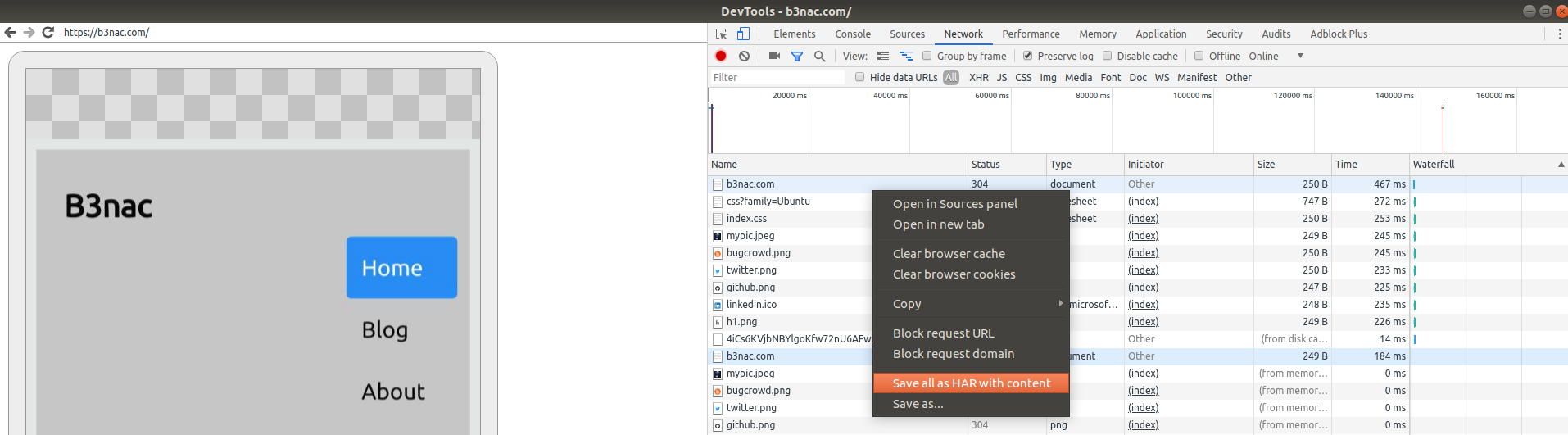
Further exploration
I didn't just stop at getting an ad, naturally I wanted to know more my curiosity was at an all time high. This is where I get an adrenaline rush, when I'm digging deeper into an application or method. In this case it was a malvertising campaign.
After following the redirect I was presented with another page posing as a Reward Center. I downloaded the page and it was 4134 lines long, this in itself was interesting. Secondly the file extension was ".mhtml". After looking up the mhtml file format this makes total sense as to why this file format was chosen. The summary of a mhtml file is "a web page archive format used to combine, in a single computer file, the HTML code and its companion resources that are represented by external hyperlinks in the web page's HTML code".
I soon found out the hyperlinks for the redirects were in the Multipart Boundaries section of the Rewards Center source code.
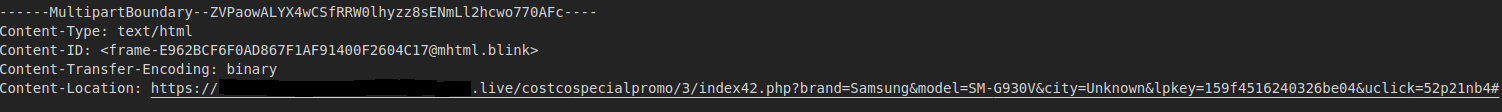
Fake comments were hardcoded into the page.
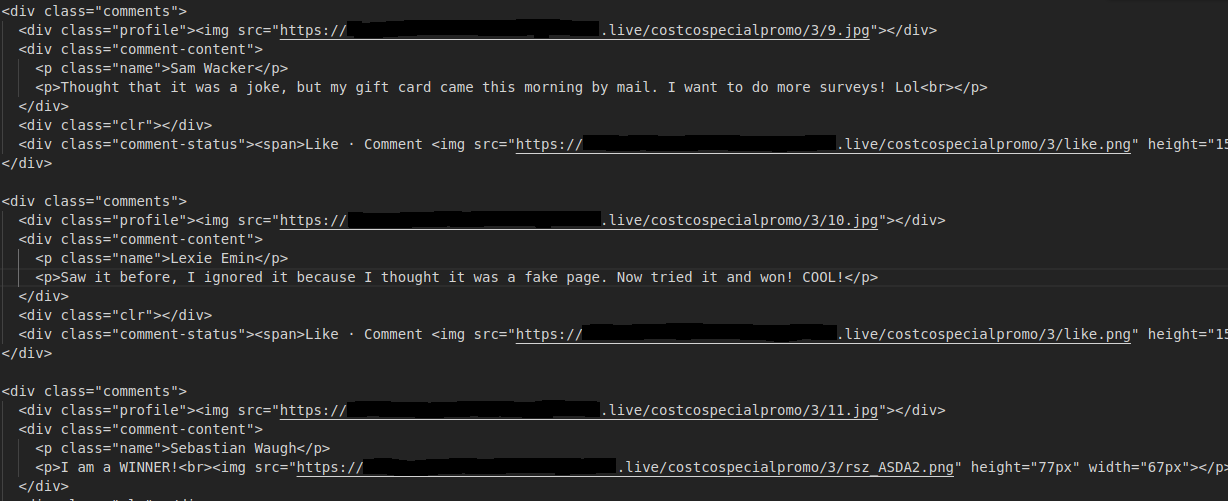
Glypicons were being used, maybe for encoding the payload to prevent detection.
Finally found the image data near the bottom of the file! Looks like some of the data is encoded by Glyphicons.
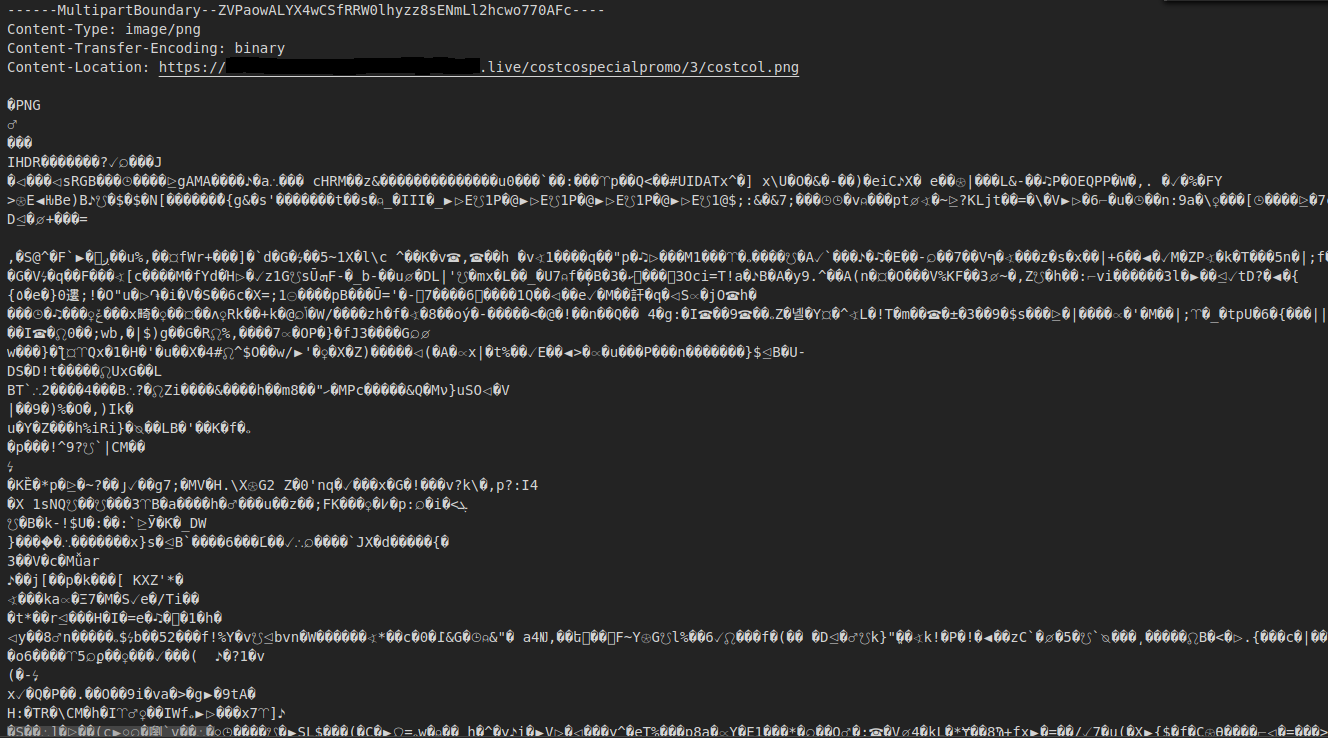
I believe the payload polyglots are here but heavily obsfucated. One of the reasons is that Javascript comments are terminated with "*/" and It's in two of these images.

My goal is to decode these image payloads and have a part 2 to this blog post. I hope you enjoyed this write up as much as I enjoyed hunting for malvertising ads.
P.S. I'm currently looking for a job, if you like my work please reach out to me at [email protected] or my LinkedIn.
Resources
https://developers.google.com/web/tools/chrome-devtools/remote-debugging/